- Published on
Authentication Context
- Authors

- Name
- Simon Håkansson
- @0fflinedocs
Authentication Context
Authentication Context is a feature in Conditional Access that grants the security admin the ability to protect actions and data in cloud applications. In this blog post I'll break down some of the use cases and benefits of authentication context and how it can work together with Authentication Strength.
Benefits & Support of Authentication Context includes:
- Accessing a Sensitive App
- Entra ID Role Activation (PIM)
- Group Membership Elevation (PIM)
- Accessing data in Sharepoint Online
- When accessing specific data in Sharepoint, authentication context can enforce stricter security policies.
- Custom applications
- You can also integrate authentication context with your own custom-built applications.
The Relationship Between Authentication Strength & Context
Authentication Strength defines the required combinations of authentication methods.
Authentication Context defines when and where such access will be enforced.
Strength and context can be used together or separately depending on the scenario.
Scenario: Step-up authentication during Entra ID role activation in PIM
In this example we will ensure that we require re-authentication in PIM on every elevation (context) and at the same time we require Phishing-Resistant MFA (strength).
To achieve this, a few steps are required:
- Create our authentication context
- Publish it to apps (ensuring that PIM can access and use authentication context)
- Create a Conditional Access policy targeting our context and enforcing our authentication strength
- In this example, the target role is Global Administrator, with the requirement Phishing-Resistant MFA and Sign-in frequency - Every time
NOTE
I recommend that you maintain consistency between authentication strength and context names for easier management.
Suggestions include Compliant device or Phishing-Resistant MFA since the context might be assigned and used on multiple resources.
Create an Authentication Context using Powershell & Microsoft Graph
The script below creates a new Authentication Context in Entra ID.
Context name: Require Phishing-Resistant MFA (Context)
Description: Require Phishing-Resistant MFA
Published to apps: Yes
ID: C66
# Check if Microsoft.Graph.Identity.SignIns module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Beta.Identity.SignIns)) {
# Install the Microsoft.Graph.Identity.SignIns module if not installed
Install-Module Microsoft.Graph.Beta.Identity.SignIns -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Beta.Identity.SignIns module is already installed."
}
# Check if Microsoft.Graph.Authentication module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Authentication)) {
# Install the Microsoft.Graph.Authentication module if not installed
Install-Module Microsoft.Graph.Authentication -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Authentication module is already installed."
}
# Connect to MS Graph with the specified scope for authentication context creation
Connect-MgGraph -Scopes "AuthenticationContext.ReadWrite.All"
# Define the parameters for the new Authentication Context
$params = @{
id = "c66"
displayName = "Require Phishing-Resistant MFA (Context)"
description = "Require Phishing-Resistant MFA"
isAvailable = $true
}
# Create a new Authentication Context in Entra ID
New-MgBetaIdentityConditionalAccessAuthenticationContextClassReference -BodyParameter $params
Source: Github
Assigning the context in Privileged Identity Management
Navigate to Entra Privileged Identity Management
Role Activation
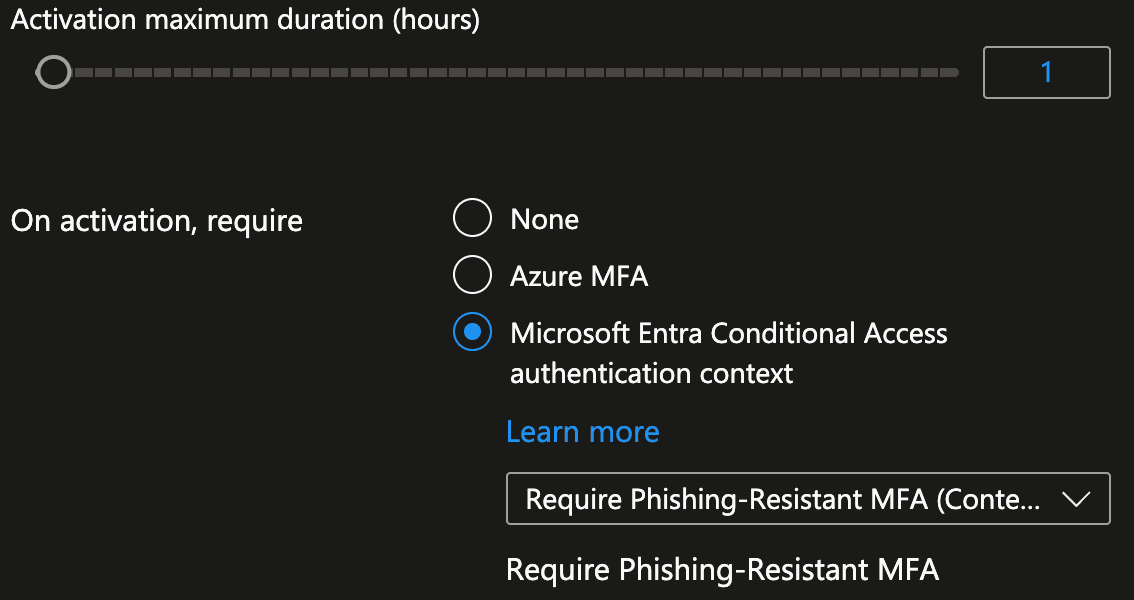
Privileged Identity Management > Manage Roles > Global Administrator > Settings > Edit
NOTE
Change your activation duration based on your needs, in this case I set activation time for 1 hour for Global Administrator.
Creating our Conditional Acces Policy targeting Global Admin
Finally we will create a Conditional Access Policy that uses our newly created authentication context & built-in authentication strength.
This policy enforces a step-up authentication (phishing-resistant MFA) when the role Global Administrator is activated in PIM.
This script creates a conditional access policy with the following properties:
Name: GRANT - Require Phishing-Resistant MFA (Authentication Context)
Target Role: Global Administrator
Authentication Context: Require Phishing-Resistant MFA (Context)
Authentication Strength: Phishing-Resistant MFA (built-in)
Session: Sign-in frequency - Every time
# Check if Microsoft.Graph.Identity.SignIns module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Beta.Identity.SignIns)) {
# Install the Microsoft.Graph.Identity.SignIns module if not installed
Install-Module Microsoft.Graph.Identity.SignIns -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Identity.SignIns module is already installed."
Import-Module Microsoft.Graph.Identity.SignIns
}
# Check if Microsoft.Graph.Authentication module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Authentication)) {
# Install the Microsoft.Graph.Authentication module if not installed
Install-Module Microsoft.Graph.Authentication -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Authentication module is already installed."
}
# Connect to Microsoft Graph with the specified scope for conditional access policy creation
Connect-MgGraph -Scopes "Policy.Read.All", "Policy.ReadWrite.ConditionalAccess", "Application.Read.All"
# The properties of the conditional access policy, converted to hashtables
$policy = @{
displayName = "GRANT - Require Phishing-Resistant MFA (Authentication Context)"
state = "enabledForReportingButNotEnforced"
conditions = @{
clientAppTypes = @("all")
applications = @{
includeAuthenticationContextClassReferences = @("c66")
}
users = @{
includeRoles = @("62e90394-69f5-4237-9190-012177145e10")
}
}
grantControls = @{
operator = "OR"
authenticationStrength = @{
id = "00000000-0000-0000-0000-000000000004"
displayName = "Phishing-resistant MFA"
description = "Phishing-resistant, Passwordless methods for the strongest authentication"
policyType = "builtIn"
}
}
sessionControls = @{
signInFrequency = @{
authenticationType = "primaryAndSecondaryAuthentication"
frequencyInterval = "everyTime"
isEnabled = $true
}
}
}
# Create the conditional access policy with the specified properties
New-MgIdentityConditionalAccessPolicy -BodyParameter $policy
Source: Github
The next time the Global Administrator role is activated in PIM, this step-up authentication will be prompted ensuring we meet the requirements of Phishing Resistant-MFA.
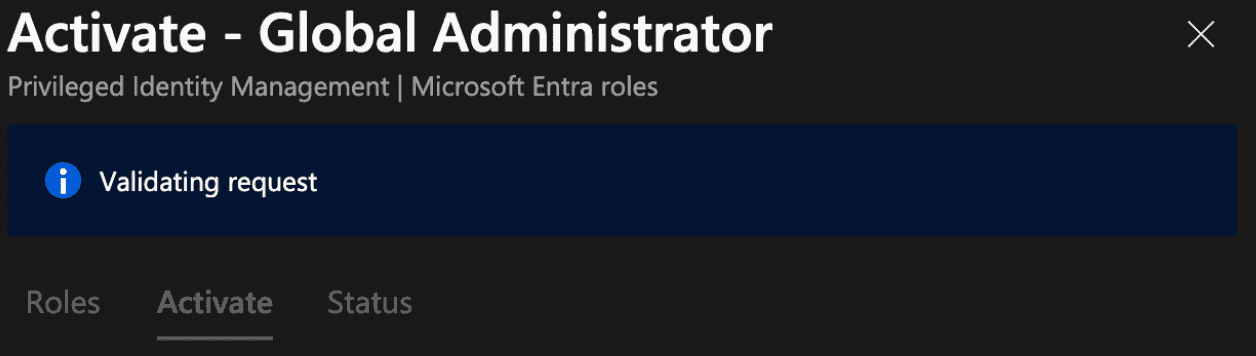
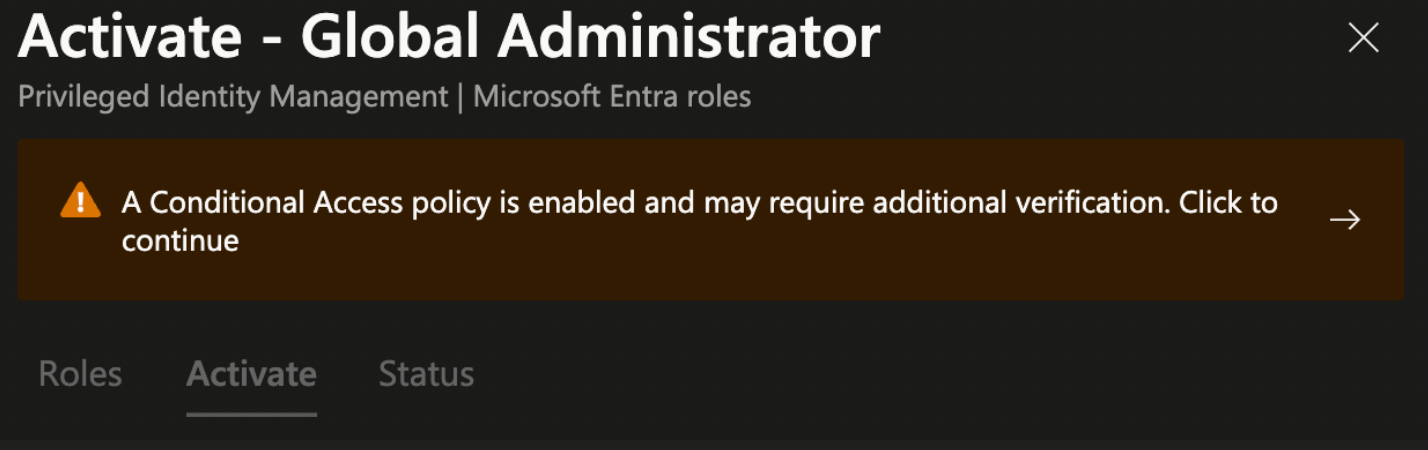
Group Membership Activation
We can also assign the context for group membership elevation in PIM, not only specific roles. Privileged Identity Management > Manage Groups > Select Group > Settings > Member or Owner > Edit > Select & Apply Context
Summary
To summarize, this is yet another tool to be used to strengthen your identity security posture in Entra ID.
Authentication Context let's us secure sensitive data and actions in a granular way.
It also supports a flexible implementation which is great!
Remember that you can use built-in authentication strengths, or define your own.
For additional Context recommendations: See this script.