- Published on
Authentication Strength
- Authors

- Name
- Simon Håkansson
- @0fflinedocs
In this blogpost I will briefly cover authentication combinations and the use case & benefits of Authentication Strength.
Authentication Method Combinations
Different combinations of authentication methods in Entra ID yield different levels of protection.
Phishing-Resistant MFA is the strongest available method for protection against phishing and token theft.
| Authentication method combination | MFA | Passwordless | Phishing-resistant MFA |
|---|---|---|---|
| Passkey / FIDO2 Security Key | ✅ | ✅ | ✅ |
| Windows Hello for Business | ✅ | ✅ | ✅ |
| Certificate-based authentication (Multi-Factor) | ✅ | ✅ | ✅ |
| Microsoft Authenticator (Phone Sign-in) | ✅ | ✅ | |
| Temporary Access Pass | ✅ | ✅ | |
| Password + something you have | ✅ | ||
| Federated Multi-Factor | ✅ | ||
| Certificate-based authentication (single-factor) | ❌ | ||
| SMS sign-in | ❌ | ||
| Password | ❌ |
NOTE
MFA - traditional MFA (Microsoft Authenticator with Notification/Number Matching).
Passwordless MFA - satisfies MFA but does not require a password.
Phishing-resistant MFA - requires an interaction between the authentication method and the sign-in surface (hardware-bound).
Authentication Strength
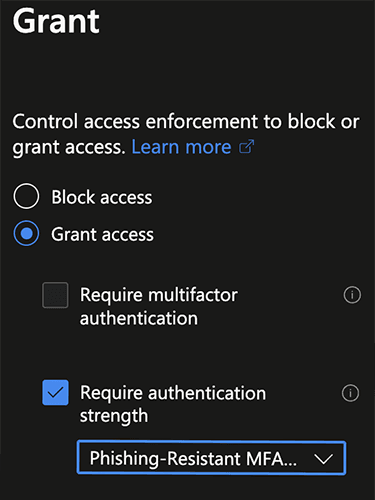
Authentication strength lets us define and use different combinations of authentication methods.
These are then applied in Conditional Access Policies to enforce granular authenticaiton requirements.
This is an example built-in authentication strength from Entra ID:
Phishing-Resistant MFA (built-in method)
Windows Hello For Business
OR
Passkeys (FIDO2)
OR
Certificate-based Authentication (Multifactor)
Another common custom example includes Temporary Access Pass:
Phishing-Resistant MFA + TAP
Windows Hello For Business
OR
Passkeys (FIDO2)
OR
Certificate-based Authentication (Multifactor)
OR
Temporary Access Pass (One-time use)
TIP
Temporary Access Pass is required to support a passwordless onboarding experience for employees.
Create Authentication Strength using Powershell & Microsoft Graph
Use the code below to create a new custom Authentication Strength in Entra ID.
Example below includes WHfB, Passkeys incl. FIDO2 & Temporary Access Pass (one-time use).
# Check if Microsoft.Graph.Identity.SignIns module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Identity.SignIns)) {
# Install the Microsoft.Graph.Identity.SignIns module if not installed
Install-Module Microsoft.Graph.Identity.SignIns -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Identity.SignIns module is already installed."
}
# Check if Microsoft.Graph.Authentication module is installed
if (-not (Get-Module -ListAvailable -Name Microsoft.Graph.Authentication)) {
# Install the Microsoft.Graph.Authentication module if not installed
Install-Module Microsoft.Graph.Authentication -Scope CurrentUser -Verbose
} else {
# Output a message if the module is already installed
Write-Output "Microsoft.Graph.Authentication module is already installed."
}
# Connect to MS Graph with the specified scope for authentication method policies
Connect-MgGraph -Scopes "Policy.ReadWrite.AuthenticationMethod"
$policy = @{
displayName = "Phishing-Resistant MFA + TAP"
description = "WHfB, Passkeys incl. FIDO2 & Temporary Access Pass"
requirementsSatisfied = "mfa"
allowedCombinations = @(
"windowsHelloForBusiness",
"fido2",
"temporaryAccessPassOneTime"
)
}
New-MgPolicyAuthenticationStrengthPolicy -BodyParameter $policy
Source: Github
NOTE
Depending on your scenario, one-time use of TAP won't be enough. Be sure to test and verify your onboarding process.
Requires Conditional Access Administrator or Security Administrator
Summary
Authentication Strength in Conditional Access is a powerful tool that gives you granular control over how users access your organization's resources.
Since authentication strength is customizable and modular in terms of where we can apply it, we have many options yo secure our organization.
I recommend that you consider implementing Phishing-Resistant MFA for your administrators & endusers.
Authentication strength gives us the ability to do it in a flexible manner.