- Published on
Remediate Credential Guard
- Authors

- Name
- Simon Håkansson
- @0fflinedocs
This blog post will cover how you can use Remediations in Intune when Credential Guard reports as "Not Applicable" on Windows Devices.

Recently in an environment we noticed plenty of errors on different Endpoints within Endpoint Security from the Windows 10 MDM Security Baseline. Assignment status reports back as Error and digging a bit deeper on the individual settings of the Security Baseline per endpoint, Not applicable was the status for these values:
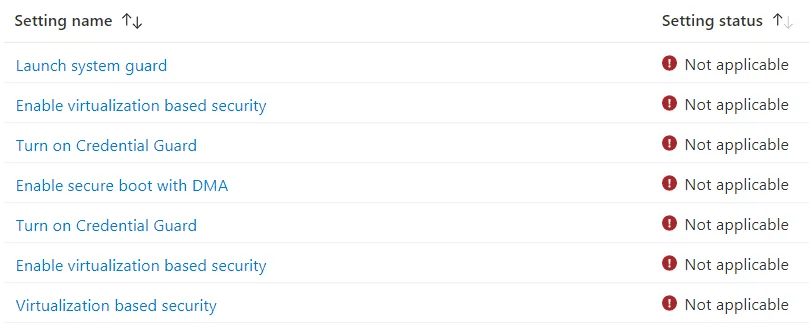
Since the status is not applicable, are all requirements fulfilled?
A quick recap on the requirements of Credential Guard:
- 64-bit CPU with support for Virtualization-based security
- Secure Boot
- Trusted Platform Module (TPM)
- UEFI-Lock (recommended)
- Windows 10 Enterprise License (to support Virtualization based security features)
Investigation
Locally we have multiple options of verifying that Credential Guard and it’s requirements are correct.
Powershell
With the Win32_DeviceGuard Class we can collect information about the current status. See example output below:
$CredentialguardStatus = (Get-CimInstance -ClassName Win32_DeviceGuard
-Namespace root\Microsoft\Windows\DeviceGuard)
$CredentialguardStatus.SecurityServicesConfigured
0: Windows Defender Credential Guard is not configured.
1: Windows Defender Credential Guard is configured.
$CredentialguardStatus.SecurityServicesRunning
0: Windows Defender Credential Guard is not running.
1: Windows Defender Credential Guard is running.
Event Log
Application and services log/Microsoft/Windows/Device Guard
Fixing The Issue
Considering that the values reported back of the Security Baseline stated “Not Applicable”, the Windows Enterprise-license came to mind. Rightly so, after verifying these users they did not have their Windows Enterprise-license assigned to them (their devices were provisioned earlier). Strangely enough assigning the Enterprise license and rebooting their machines did not mitigate the issue. To solve this issue, we have a few options. We can use an application, a regular Powershell script or Remediations. In this case I decided to go with Remediations.
To mitigate the issue, add these remediations. Test and verify on a few select devices before rollout in production. If you are unsure, start by deploying the Detection script only to detect the current output on devices (this has no impact).
Checks status of Credential Guard services and returns output based on if services are configured, running or not. If virtualization based security is not running the script return that information and then exit. If required registry settings for Credential Guard are missing the script will return the script for Remediation.
The remediation script will remove certain Credential Guard related registry keys related to Intune-reporting and will also add required Credential Guard configuration into the registry (UEFI Lock Enabled). Important! After the remdiation has executed a reboot will be required for proper configuration and reporting.